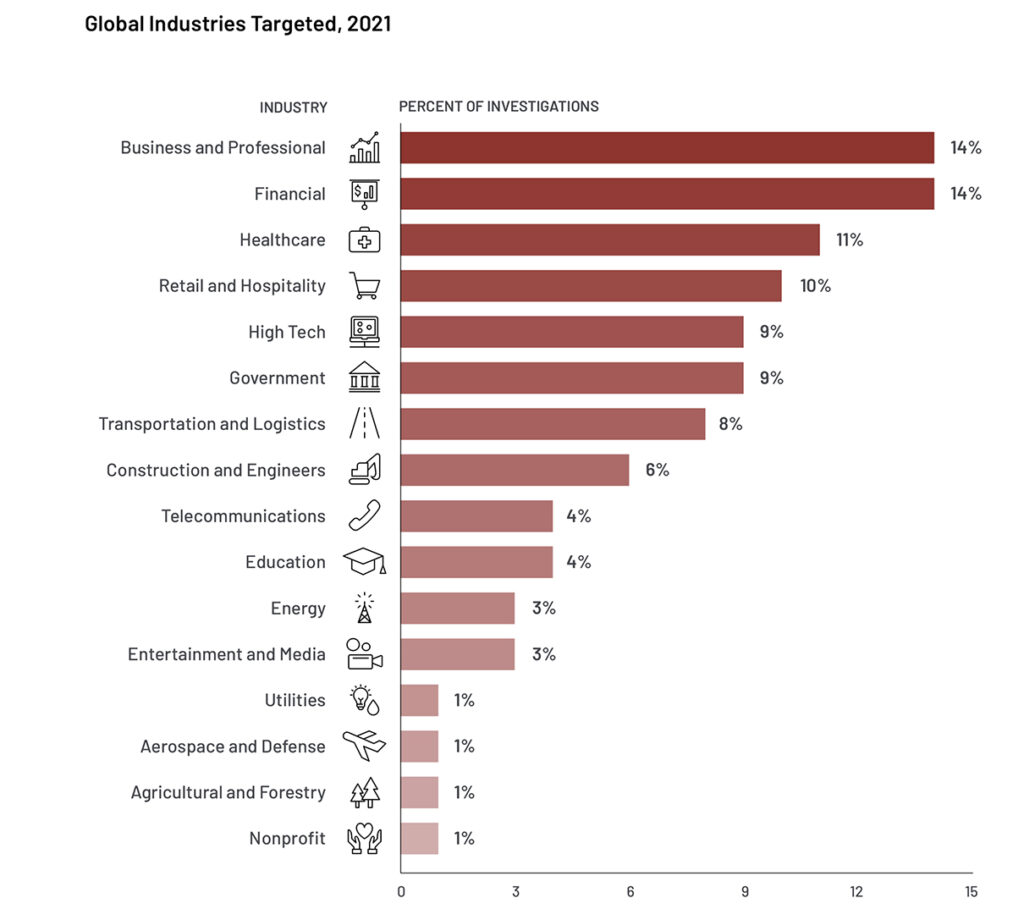
If your organization offers financial, healthcare, business, or professional services, you face a high risk of a cyber attack, according to a recent report from Mandiant, a global security company. On the other hand, utilities, aerospace, agricultural and nonprofit organizations are much less frequently targeted by cybercriminals.
“Adversaries typically aim for financial gain through extortions, such as ransomware, or the theft of data,” said Regina Elwell, senior principal threat analyst, Mandiant, at April 27 BrightTalk webinar on “Today’s Top Cyber Trends and Attacks: By the Numbers.”
Her colleague, Kirstie Failey, senior threat analyst, added that criminals prefer digital tools that are readily available and easy to use.
In the webinar, the two analysts provided highlights of the “M-Trends 2022” report, based on Mandiant’s frontline incident response experience and threat intelligence from October 1, 2020 to December 31, 2021.
“One of the biggest surprises was a reduction in investigations involving phishing attacks,” said Elwell. In response to a question, she noted that while voice channels remain a potential vehicle for cyber attacks, she did not recall any incidents in the firm’s data set for the report.
Key trends
One of the key findings of the Mandiant report was a win for defenders, as the global median dwell time declined in 2021. For investigated intrusions, the median time between compromise and detection was 21 days., down from 24 days in 2020, and 60 weeks in 2011.
Although this may demonstrate improved visibility and response, Elwell said the pervasiveness of ransomware attacks drove dwell times down. “These attackers move much more quickly than traditional espionage intrusions,” she added. “Once they get their malware in place, they announce their presence.”
In 2021, there was a global decline in ransomware instructions, despite an increase in the Asia-Pacific (APAC) region, Elwell said. That reflected the widespread impact of the 2020 ransomware attacks using Sunburst and Solar Winds infection vector.
Data theft was a primary mission objective in 29 percent of intrusions, as attackers sought to resell the stolen information or use it as leverage in payment negotiations with the target organization, Elwell said. Supply chains were compromised in 17 percent of intrusions in 2021 compared to less than 1 percent in 2020, pointing to the need for tight security when working with vendors.
According to the report, last year Mandiant responded to more than 20 incidents involving exploitation of on-premises Microsoft Exchange servers. Critical vulnerabilities, such as “Log4Shell,” highlight the dangers and the importance of patching, Elwell said.
On the positive side, Elwell said there was a 12 percent drop in the use of phishing attacks last year. “That speaks to the ability of organizations to detect and block emails, as well as providing training for employees,” she said. “I don’t think phishing will ever go away, but it is not as effective for adversaries as it used to be.”
Summing up the report’s findings, Failey said organizations need to pay close attention to trends in cyber attacks so that they can protect themselves appropriately against the most prevalent techniques. As she said, “Organizations today must balance the convenience and accessibility of common technologies with the best possible cybersecurity measures.”
