Cyber attackers typically follow certain patterns when trying to breach session border controllers (SBCs) and penetrate an organization’s network. That makes it imperative for IT professionals to monitor communications applications and respond quickly to prevent toll fraud, data theft and other types of attack.
“SBC monitoring in real-time is vital to keeping your UC/CC network safe,” said Dr. Val Matula, chief technical officer, Assertion, at an Avaya ENGAGE 2021 session, “Top 10 Attack Vectors That Breached Session Border Controllers (SBCs) in 2021 and How to Prevent Them.”
For instance, Matula said one set of hackers might break into the network, and then sell that access to a second group of cybercriminals. “Be on alert for someone registering from a country in Eastern Europe, for example, and 10 seconds later registering from the Middle East,” he said. “That’s impossible without time travel – and a clear sign of an immediate threat.”
Top attacks against SBCs
In his talk, Matula outlined the top attacks against SBCs with examples drawn from a variety of verticals showing typical techniques to gain access to the network.
• Toll fraud. A major healthcare organization was penetrated by attackers who were able to use social engineering techniques to find a phone number and identify a vulnerable extension. “The hackers were able to drive calls to an international premium rate number at $3 a minute,” Matula said. “The carrier was able to shut them down, but that resulted in business problems for the organization.”
• Data exfiltration. A major city’s transportation authority was subjected to an attack after broke into the phone system, determined the password pattern and took control of about 50 extensions. “The hackers took a passive approach. They registered the extensions to foreign locations without activities, and listened to active calls as a second extension, pulling information from those conversations,” Matula said.
• Harassment. A leading European retailer was victimized when an attacker impersonated a company employee and made hundreds of calls harassing female members in the local community. Although no data was stole, the attack had a damaging impact on the company’s reputation.
• Journal tampering. An attacker broke into the administrator’s login, and was able to change the configuration of the SBCs, deleting or editing logs to cover the break-in.
• Endpoint imitation. After registering, an attacker stole the endpoint configuration file, and was able to listen to confidential calls. If a business deal was underway, for instance, advance notice of that transaction might be very valuable to sell to an investor, Matula said.
• Biometric leaks. An attacker listened to the IVR and agent interactions, then used voice recordings to get past biometric password processing. This type of attack could provide access to confidential customer information and interactions.
• Telecom denial of service. Attackers have created scripts to pound an SBC with brute force attack or misconfigure a server to send bad messages to the SBC, causing havoc within the enterprise.
• Data leak. An attacker who successfully broke in as an administrator could then take control of customer interactions, asking for credit card numbers and personal data that could be sold on the dark web. “The company itself wouldn’t see anything, as the only evidence would be outside from the customers,” Matula said.
Securing the perimeter
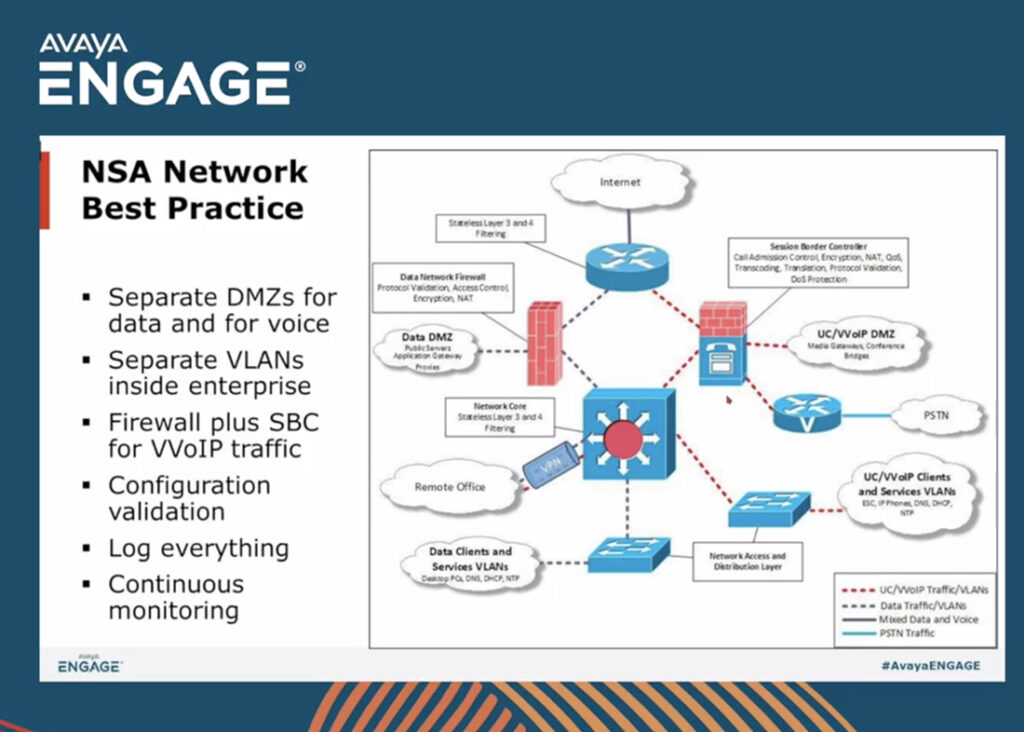
Based on these attack patterns, Matula has several suggestions to secure the perimeter. “Log everything and monitor your network continuously,” he said. “You should also separate the voice and data DMS, and hide your network topology.”
Other tips include tracking user location – especially if there are sudden changes in an extension’s site, and looking at registration attempts. “If you see 20 attempts at one extension before a proper registration, then sent a password reset right away.
For more information about SBC threats, Matula said Avaya and other vendors offer tools for inspection and monitoring. In addition, the National Security Agency (NSA) has established guidelines on perimeter security, and organizations have collaborated to establish the MITRE ATT&CK® framework is a curated knowledge base and model for cyber adversary behavior. As Matula said, “Learn from others. You don’t have to invent the wheel.”
