Have you confirmed the identity of everyone participating in your virtual conference session? If you are transcribing or recording the event, is that data stored securely? Those are just two of the unified communications and collaboration (UC&C) security challenges facing IT professionals – particularly when consumer devices and applications are added to enterprise-grade solutions.
“UC security implementations are complex because no single solution exists for multiple platforms or tiers of service,” said Sorell Slaymaker at a recent Enterprise Virtual Connect session on “Unified Communications and Collaboration Security.” As principal consulting analyst for TechVision Research, Slaymaker laid out the security challenges and risk mitigation solutions in a conversation with Eric Krapf, general manager and program co-chair, Enterprise Connect.
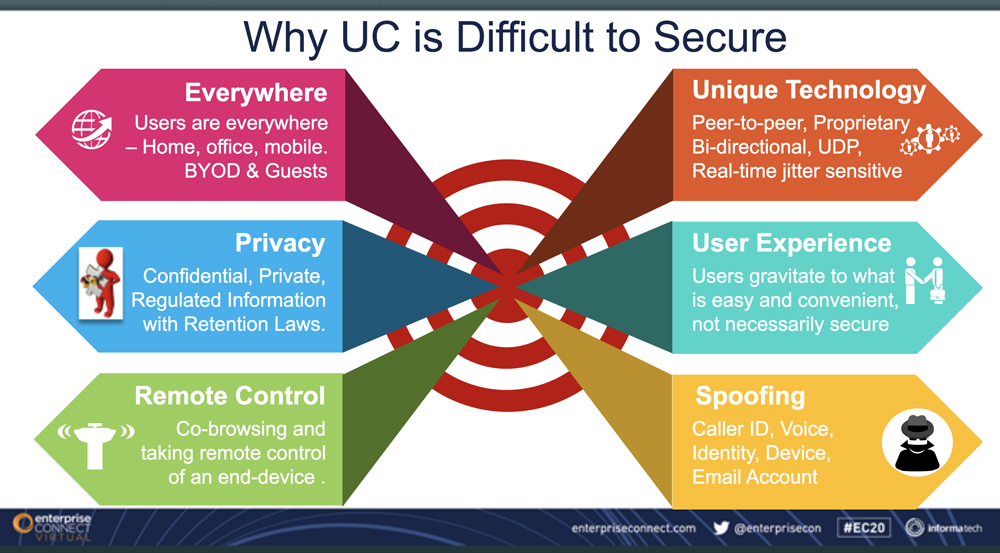
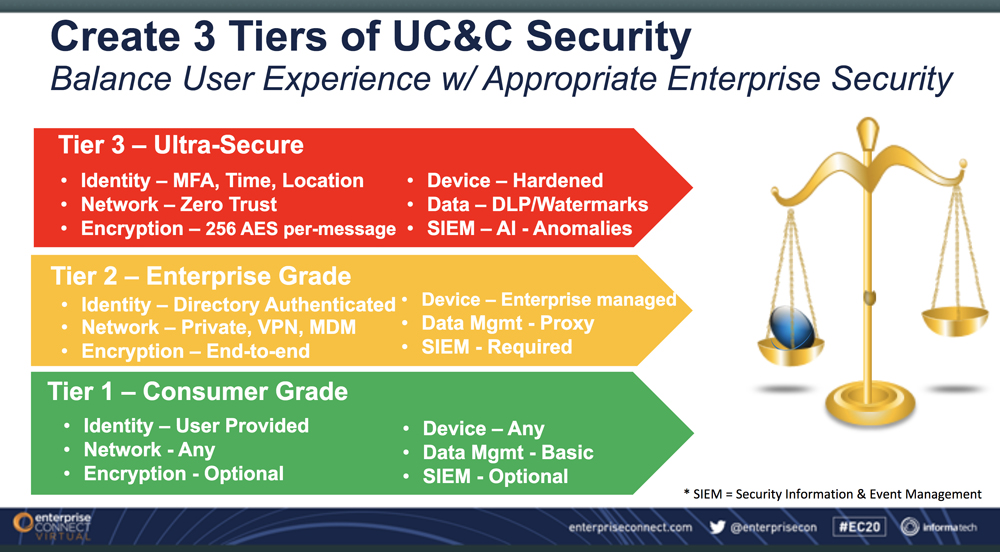
“Architects, engineers, and managers have to work together to incorporate UC&C’s unique security challenges into the overall enterprise security program,” said Slaymaker. However, security must be balanced with the user experience. “If you make things too difficult for the users, they will gravitate to something easier and bypass your security arrangements.”
UC&S security issues include authenticating the identity of remote participants, including users and guests. “The foundation of all good security is access and identity management,” Slaymaker said. “If someone spoofs an identity, all controls are off.”
Slaymaker said video conferencing is a new channel for phishing attacks where participants are asked to provide personal information in an environment that seems secure. Co-browsing is another potential risk as an unauthorized participant could gain access to someone else’s computer and data. “It’s not just the written data,” he added. Spoken words or images might also contain clues that could be exploited by criminals.
“You can also be compromised by your business partners,” he added. “It’s not only your front door to the Internet, but the back doors as well.”
One potential solution is adding location to the authentication process, said Slaymaker. “A device with an IP address can be linked with a wifi or a GPS identification,” he said. “The nice thing about his approach is that it doesn’t require anything from the user, and it can’t be taken away by a thief. If you have trade secrets and only want people at a certain manufacturing plant to have access to that data, you could use this approach to grant access to a user at that location.”
UC&C security doesn’t end when the virtual session is over. “About 30 percent of conferencing sessions are being recorded, creating additional data that needs to be secured,” he added. “If you record something, you have to think about how to secure it. That might mean not doing the recording at all.”
You can also use post-conference reports to identify any anomalies, such as an “invisible” participant or someone who joined midway through the session without registering.
Other UC&C issues include spoofing phone numbers or voices. Slaymaker cited the example of an IT professional who answered a call and heard, “This is your wife. I’m at the store and need your credit card number.” When he asked the caller, “What is the name of our cat?” the fraudster hung up.
Security risks include downloading apps that could contain malware, leaving devices unattended in a public location, and even installing new gateways or routers. “There have been several incidents where hardware shipments were intercepted on the way to a business and malware added before reaching the destination,” he said.
“Never underestimate the inventiveness of the crooks who do this for a living,” said Slaymaker. “Cyber crime is a $1 trillion global industry and the threats will continue to grow. We have to keep evolving quickly to stay ahead of the criminals.”
